Code Obfuscation is a powerful technique in the world of software development and cybersecurity that helps protect sensitive code against malicious tampering and reverse engineering of the software application. Obfuscation is also called ‘Obfuscation’ and it is a method that makes the source code of a program harder to read or interpret by using various techniques. Code Obfuscation is an intriguing concept; one that is very relevant in this highly technology-driven world that we live in today.
Understanding Code Obfuscation
Code Obfuscation is the act of deliberately hiding the source code of a program without changing its behavior. It is the process of making some changes and manipulations for the code to be challenging to read, analyze, and unwind. The main objective of Code Obfuscation is to discourage possible malicious attackers and safeguard the confidentiality of the data contained in the software.
As cyber threats continue to grow more complex, there is a possibility that such applications as reverse engineering, intellectual property theft, and security breaches can be directed at such companies. This is important because it stands up to these threats. This helps ward off intruders by making it very difficult for them to crack the code, thereby enhancing the security of the application altogether.
The Significance of Code Obfuscation
Intellectual Property Protection: Software being developed and invested with time and resources becomes very important to an organization. The first benefit is code obfuscation which protects proprietary algorithm, business logic, and other vital code components from copying or replication by rivals.
- Security Enhancement: Strengthening the security of an application is enhanced by obfuscating the code. This makes it hard for malicious actors to identify vulnerabilities, inject malicious code or exploit weaknesses in the software.
- Anti-Piracy Measures: Software piracy is still a persistent challenge in the digital age. By obfuscating code, pirates seeking to crack and redistribute unauthorized copies can be hindered, thus securing income streams.
- Protection Against Reverse Engineering: One of the favorite tactics employed by hackers is reverse engineering software. The use of Code Obfuscation brings in complexness and makes it considerably harder for attackers to reverse engineer and appreciate the intricacies of an application.
Techniques of Code Obfuscation
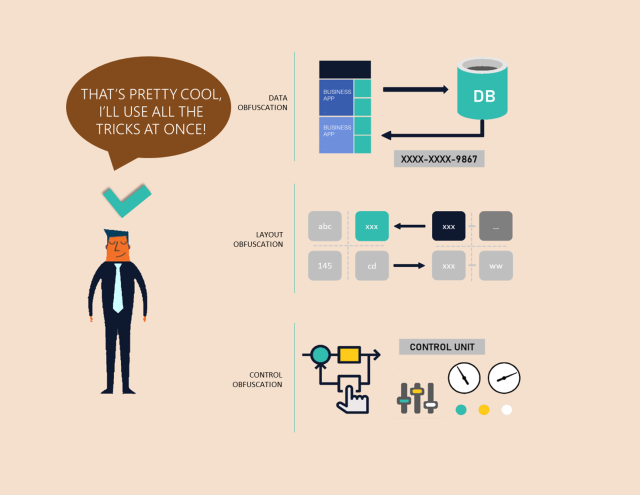
Code Obfuscation uses many techniques that make the source code confusing. The techniques convert the code structure thereby making it difficult to comprehend and resistant to any form of analysis. Here are some commonly used Code Obfuscation techniques:
- Renaming Variables and Functions: It involves re-naming variables, functions and classes to make them difficult to recognize from their initial use. Random and irrelevant labels replace meaningful names that makes it difficult to understand the code.
- Control Flow Obfuscation: Logical flow is disrupted by control flow obfuscation. It injects redundant loops, conditional expressions, and jumps that complicate tracing the actual trail of the program execution.
- String Encryption: The code encrypts sensitive strings like API keys or cryptographic constants. Thus, attackers cannot take the valuable information directly out of the code.
- Code Splitting and Reordering: The program flow is interrupted by segmenting and rearranging code sections. It has made it difficult for reverse engineers to interpret the logic of the code.
- Dead Code Insertion: The application is loaded with unused or “dummy” code. This, not only, muddies the code but confuses others trying to study it.
- Constant Encryption: The numeric constants are encrypted or substituted by mathematical expressions. This method prevents attackers from interpreting the meaning of these constants.
- Anti-Debugging Techniques: Among such mechanisms are those that detect debugging attempts and interfere with debugging tools in order to make it more complicated for an intruder to analyze the code.
- Dynamic Code Generation: For example, some of them generate code during runtime, making it practically impossible for analysis instruments to understand it.
Benefits of Code Obfuscation
Implementing Code Obfuscation offers a range of benefits for software developers and organizations:
- Protection of Intellectual Property: Code Obfuscation is used for protecting the valuable intellectual properties so that no competitor or adversary can easily copy or reverse engineer the proprietary code.
- Enhanced Security: Code Obfuscation makes it difficult for attackers to read code, alter code, and exploit vulnerabilities or security threats.
- Mitigation of Piracy: Unreadable code, on its hand, makes it harder to produce copies of software intended for pirating.
- Reduced Attack Surface: Exploiting vulnerabilities in code is dependent on understanding it. By reducing the attack surface, code obfuscation hinders accessibility of the code for exploitation.
- Increased Competitive Advantage: By using Code Obfuscation, one can protect their software in order to have the upper hand over others in terms of maintaining one’s exclusive features and operations.
Challenges and Considerations
While Code Obfuscation is a powerful tool for enhancing software security, it is essential to be aware of potential challenges and considerations:
- Performance Impact: Complexity brought in code may slow down performance and make application execution sluggish. Security must be balanced with performance when developing.
- Debugging Difficulties: Debugging may become difficult for legitimate developers because their variable names and the program flow are obfuscated while using Code Obfuscation.
- Compatibility Issues: However, obfuscation might sometimes get in the way of third-party libraries or frameworks and therefore pose compatibility challenges that must be handled with caution.
- Cost and Complexity: There’s also the potential for added man hours or costs that may be necessary when implementing Code Obfuscation. Organizations should assess the economic feasibility of obfuscation within their specific settings.
- Maintainability: Making code hard to maintain and update through code obfuscation. Obfuscated code must also be documented, so that it is effective to manage any future development effort.
Conclusion
As software security becomes crucial in the digital age, Code Obfuscation is a powerful companion. It helps developers and other organizations safeguard their intellectual property, improve application security, and counter the hazards of reverse engineering and tampering.Code Obfuscation raises challenges and concerns, but it remains a critical mechanism for protecting secret code and data. In an era of continuous technological advancement, Code Obfuscation acts as an important asset for safeguarding software applications against malicious interference of hackers of cybercrimes.